Easily Protect Your Files, Messages and EMails With PGP/GPG
GPG tools allow you to easily generate your own PGP key pairs for encryption, signing, etc. Here's how you can get started.
Encryption is a cornerstone of the modern internet. You use it transparently every time you pick up your device. Every video, instant message, social media post read or written is encrypted at some point along the chain, even if the contents on either end of the interaction are visible to all. This prevents bad actors from intercepting or manipulating your activities on the internet. Without encryption, things like online banking and shopping wouldn’t be possible.
Most of the encryption that takes place is transparent, handled silently in the background by the software you’re using. Even if you’re using a privacy and security focused app like Signal, you’re not manually generating and distributing your encryption keys. The most involvement you’re asked to do is to scan a QR code to log in on a new device and occasionally verify that other devices should still be allowed to have access to your messages.
And truthfully, this is how things should work 99+% of the time. Humans are, in general, terrible stewards of their own cybersecurity, so it’s better to create and use open, publicly audited systems that largely automate the processes in the background so that a bit of human error or forgetfulness doesn’t jeopardize sensitive information. This is why the US government operates logically and often physically separate networks specifically for the handling of classified information; so that it takes an intentional act of espionage or complacent carelessness to put classified information on an unclassified system. When you’re browsing the internet, every website you visit that begins with “https” is using an encrypted connection to communicate; and the establishment of that encrypted channel is handled entirely transparently by your web browser in the background within milliseconds once you enter a URL.
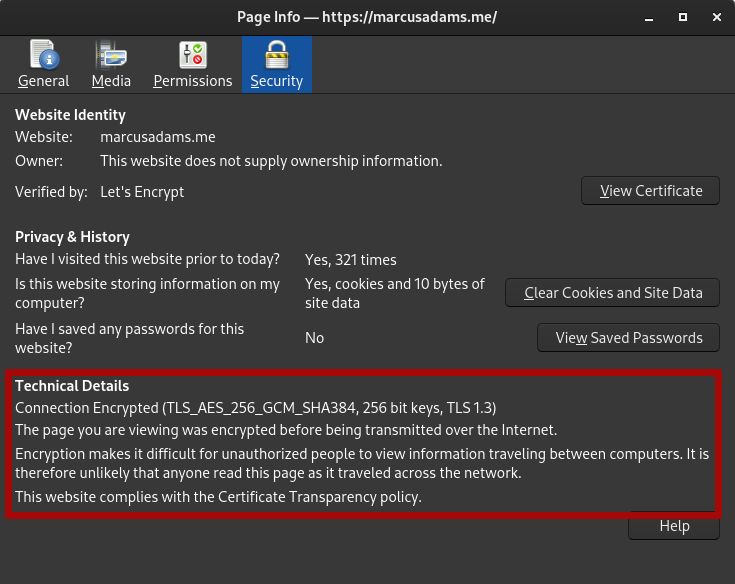
However, there are scenarios where manually handling your own encryption and signing keys can be useful and beneficial. Let’s say you need to send a sensitive file to someone, but the means by which you have to send it are untrustworthy. Let’s say you created something and you want to prove that you created it AND that it hasn’t been modified since you made it? That’s where a tool like PGP comes in.
PGP stands for “Pretty Good Privacy”, and has been around for ages. It’s primarily used as a mechanism to facilitate using “asymmetric” encryption which allows you to both encrypt and decrypt files and information, but also prove authorship thru a process called “digital signatures”. There are a variety of different tools available, but they all generally interact with the same underlying, interoperable standards. So whether you see PGP, OpenPGP, GnuPG, GPG or LibrePGP, you can mostly consider them basically interchangeable for all intents and purposes.
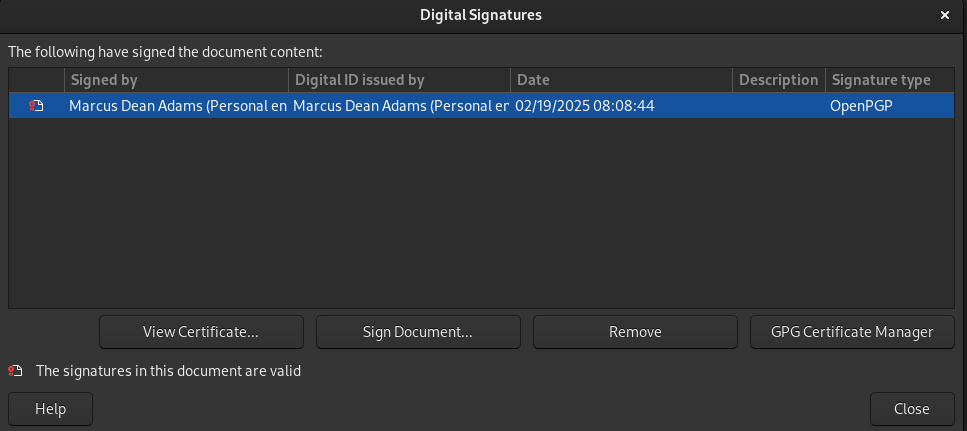
So if you want to start using PGP, you first need to understand the basics of how it works.
Let’s say Bob and Alice wish to exchange private messages with one another using PGP. First, both Bob and Alice need to generate their own PGP “key pair”. One of these keys is the “private” key. You must protect your private key and never share it with anyone ever. The other key is the “public” key. As its name implies, this key is intended to be made public. You can post it to social media, publish it to a key server, send it in an email, whatever you want. Once Bob and Alice have generated their key pairs, they then share with one another their public keys. Then, if Bob wants to send Alice a secure message, he uses Alice’s public key to encrypt the message. He can then send this encrypted version of the message using whatever means he and Alice have agreed upon, such as email (With the right software you can even use PGP with GMail, Outlook, etc.). Once a message has been encrypted with Alice’s public key, the only person who can decrypt the message and read it is the person who controls Alice’s private key, which “should” only be Alice. This is why it’s vitally important that you protect your devices and keep your private key safe and secure. Next, when Alice wants to reply to Bob’s message, she uses Bob’s public key to encrypt her reply to him. This ensures that only Bob can decrypt and read her reply. Thus the back and forth continues; Alice encrypts messages to Bob with Bob’s public key, and Bob encrypts messages to Alice with Alice’s public key.
Next let’s imagine that Bob has created some document or other work and wants to prove that he created it and that it hasn’t been modified since creation. He can use PGP to “digitally sign” the work. Many applications and products support this. PGP digital signatures work sort of in the reverse of PGP encryption. When you use PGP to sign something, it creates a hash of the content and then uses your private key with that hash to create the signature. Just like information encrypted with a public key can only be decrypted with the private key, information encrypted with your private/secret key can be decrypted by anybody who has your public key, which as I said earlier, is safe to distribute freely and publicly. So, since Bob is the only person who has access to his private key, this means anybody can verify the signature, and that it had to be Bob that created the signature; nobody else could have done it. Any modification to the file or document after the signature is added changes the hash, which invalidates the signature, so it also prevents subsequent modifications to a work from being falsely attributed to Bob.
So if you want to use PGP, how do you get started? If you don’t know about the PGP/GPG tools your operating system already has, the easiest method on a desktop PC is to look for and install Kleopatra. On Windows you can accomplish this by just opening a command line and running:
winget install gpg4win
Kleopatra is also available on Linux distributions. There are a variety of applications that support using PGP/GPG to encrypt and sign communications, to help you generate and publish your keys, etc.. Here are some that I have either used personally, or have seen around the internet for a while. Also note that besides using your asymmetric PGP key pairs, GPG tools like the gpg command line utility, or Kleopatra, also support doing simple symmetric encryption of files using a password. So besides managing PGP/GPG keys and encryption, GPG utilities are also powerful and useful for safely encrypting backups and other data with a password.
Apps and Services That Support PGP
Kleopatra: Desktop application that lets you manage and publish PGP keys, and encrypt and sign communications with either PGP keys or with a password. Kleopatra interacts with your system’s keychain to act as a “provider” for other PGP capable applications so you only have to import your keys once instead of adding them to every single app and service you want to use them with.
OpenKeyChain: An Android application that lets you create, publish and import PGP keys. OpenKeyChain then acts as a “provider” of PGP encryption for other applications on your device so you don’t have to manually add your keys to every single PGP capable app on your device. You can also use OpenKeyChain directly to encrypt and decrypt files or plain text messages that you send and receive thru other methods.
K-9 Mail (Becoming Thunderbird Mobile): An Android eMail client that interacts with OpenKeyChain to support exchanging PGP encrypted emails.
XMPP: In addition to the newer OMEMO standard, various XMPP chat applications, such as Dino and Conversations.im, support encrypting your chats with OpenPGP, and can even “publish” your public key to the XMPP server so that other XMPP users can easily use PGP to encrypt messages to you without necessarily having to proactively share your public key ahead of time.
Mozilla Thunderbird: A desktop email client that has built in support for PGP, allowing you to encrypt and decrypt emails using PGP.
Evolution: A Linux desktop email client that has PGP support built-in, allowing you to encrypt and decrypt emails using PGP.
LibreOffice: A free and open source office suite, available for Windows, Linux and macOS, with built-in support for creating and verifying PGP digital signatures on documents.
ProtonMail: A private email provider that uses OpenPGP to protect emails. While Proton-to-Proton PGP encryption is handled automatically you can both export your ProtonMail public key for sharing, and import others’ public keys to allow PGP encrypted messaging with non-ProtonMail users.
And finally is just the gpg command line utility. This allows you to generate and import keys, encrypt/decrypt and sign/verify files. You can also use it to do simple “symmetric” encryption with a password without actually using a PGP key.
There are plenty of other applications available on a variety of platforms, but these are ones that I’m personally familiar with and have used. In fact, while Signal is our primary messenger, my wife and I use Conversations.im with OpenPGP as our secondary/backup messenger.
So what are some advantages and disadvantages of PGP/GPG versus other methods of encryption or key management?
Advantages
You control your own key infrastructure; you don’t have to trust anybody else to do things right, not get hacked or otherwise compromised, etc.
Platform agnostic. You can use basically any communication method to send an encrypted message, whether that channel is secure or not. You don’t have to use specific apps or services to relay PGP encrypted information.
PGP keys are considered “long term” keys, which means you’re not really intended to be generating new keys constantly. This is handy for opening old encrypted emails or, in my case, when I reinstall Conversations on a new phone and import my PGP key, all my old messages are automatically visible again.
Digital signatures are a useful method of proving, or disproving, authorship of a work.
Disadvantages
Since you control your own key infrastructure you are responsible for protecting and managing your private key. Any time you get a new device, get rid of an old one, etc., it’s your responsibility to safely transfer your key to the new device and purge it from the old one. If a device with your private key becomes infected with malware or hacked, consider that key compromised.
PGP keys are long term keys, which means that if it is “ever” compromised at any point, anything that was ever encrypted using it any any point in the past can now be decrypted.
So who should use PGP directly? Ideally most people shouldn’t. Thru the use of tools like Signal, OMEMO, ProtonMail, etc., ideally the general, non-tech-savvy masses should be able to choose good products and services that take care of the crypto operations in the background for them, using open source and audit-able protocols, because much like humans are terrible at making good passwords, we’re also generally bad at key management and OPSEC. That’s why having processes in place to prevent human error are so important, and why government processes protecting classified information seem like a lot of security theater; it’s all mechanisms put in place to prevent human error from causing spillage. One forgotten transfer of your private key could result in losing access to anything ever encrypted with it and having to set up a whole new key pair, share your new public key, etc. One hacked computer could mean the compromise of years worth of encrypted data or, perhaps even worse, giving someone the ability to pose as you by digitally signing fraudulent files with your compromised private key. Even Microsoft had one of their private signing keys compromised a few years ago when one of their engineers had their computer compromised, allowing hackers to breach email accounts associated with several government organizations. Key management is easy to get wrong.
That said, it does have value for everyday use; companies like Proton have proven that. PGP is open and provider agnostic so it doesn’t matter if you’re using something like ProtonMail or not. If you’re willing to exchange public keys with somebody you can exchange encrypted emails between folks on GMail, Outlook, Yahoo, etc. You can even just encrypt a block of text and send it over SMS to the intended recipient, and they could use a GPG utility on their end to turn that back into the original plain text. Plus, if you’re a nerd like me who values controlling your own services, digitally signing emails, documents or other files for proof of authorship, being able to send encrypted files or emails between services that may or may not support encryption themselves, then PGP might be for you. Many open source developers and communities use PGP/GPG to digitally sign communications as cryptographic proof that those messages did indeed come from the person you think it did. Many Linux distributions use GPG to verify the authenticity of package downloads using their built in package managers to ensure they are coming from a trusted source and haven’t been tampered with in transit. You can even add an extra password to your PGP/GPG private key so that even if the private key gets stolen somehow, it can’t be used without the password.
I personally use GPG/PGP for a few tasks in my day to day. First, I use it with Conversations.im to encrypt messages with my wife so that we don’t have to worry as much about losing chat history when we get new devices. Plus, if someone were to compromise her XMPP account somehow and get added to her OMEMO keychain without us noticing, using OpenPGP prevents them from being able to read those messages until we do notice a new device has been added and remove it. Second, I use the gpg command line tool to do symmetric password based encryption of certain file backups. I also use ProtonMail, which uses OpenPGP transparently (no manual key management on my part) to secure my email inbox. I also use GPG/PGP to digitally sign some files when I publish personal software projects to prove authorship so that as long as the digital signature on those files still checks out, people know they haven’t been tampered with. While it’s not perfect and not for everybody, PGP/GPG can be a valuable tool in your toolbox that I think more tech savvy people should consider making use of where appropriate. With AI generated articles, images and videos that are more and more difficult to tell apart from real life, being able to not only protect your private information, but cryptographically prove the authenticity of information is going to be more important than I think it has ever been in the past.
You can find my GPG keys, if you’d like to use them to contact me, or verify the signature on things I’ve created and signed, on my personal website at:
If you have any questions or feedback, I’m more than willing to help if I can; just leave a comment here or message me using one of the methods listed on my personal website.
Donate
If you’d like to donate to me, you can either become a paid subscriber thru Substack, or you can use one of the following methods.
PayPal: https://paypal.me/gerowen
Bitcoin (BTC): bc1q86c5j7wvf6cw78tf8x3szxy5gnxg4gj8mw4sy2
Monero (XMR): 42ho3m9tJsobZwQDsFTk92ENdWAYk2zL8Qp42m7pKmfWE7jzei7Fwrs87MMXUTCVifjZZiStt3E7c5tmYa9qNxAf3MbY7rD






